Simjacker: The Next Generation of Security Vulnerability
AdaptiveMobile Security
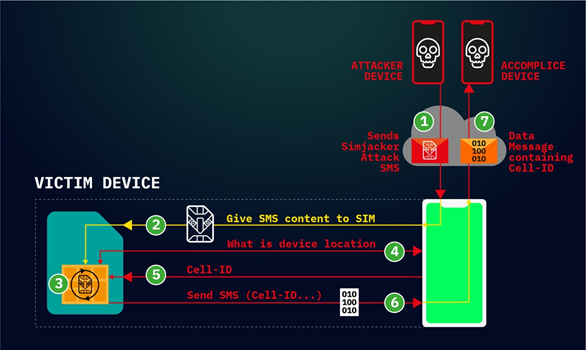
“The attack begins when an SMS - that we term the Simjacker ‘Attack Message’ - is sent to the targeted handset. This Simjacker Attack Message, sent from another handset, a GSM Modem, or an SMS sending account connected to an A2P account, contains a series of SIM Toolkit (STK) instructions, and is specifically crafted to be passed on to the UICC/eUICC (SIM Card) within the device. In order for these instructions to work, the attack exploits the presence of a particular piece of software, called the S@T Browser - that is on the UICC. Once the Simjacker Attack Message is received by the UICC, it uses the S@T Browser library as an execution environment on the UICC, where it can trigger logic on the handset."
McDaid, 2019
AdaptiveMobile Security (2019)
“Specific SMS messages targeting UICC (SIM) cards have been demonstrated before on how they could be exploited for malicious purposes. The Simjacker attack takes a different approach, and greatly simplifies and expands the attack by relying on the S@T Browser software as an execution environment. The S@T (pronounced sat) Browser – or SIMalliance Toolbox Browser to give it its full name – is an application specified by the SIMalliance, and can be installed on a variety of UICC (SIM cards), including eSIMs (McDaid, 2019).”